How ThreatInsights helps you meet your DORA requirements.

DORA requirements for Threat Intelligence
From the regulation text (esp. Articles 3, 24–27, and 45):
- Firms must have threat intelligence capabilities aligned to their business & sector.
- They must use TI to inform risk management, incident handling, and threat-led penetration testing (TLPT).
- They must have processes for collecting, analysing, and sharing intelligence (with regulators, trusted communities, and sometimes industry peers).
We built our ThreatInisghts platform to be an intelligence 1st plaform. Everything we do is built upon Cyber Threat Intelligence, it’s our base and our core. It’s not a bolt on solution, it’s built in by design.
– Andy Playford
How the ThreatInsights platform meets those requirements.
Article 3 & 45 — Threat Intelligence Capability and Information Sharing
How ThreatInsights Meets It
- Our platform provides you with curated, human-verified threat intelligence tailored to each customer’s sector and size.
- We have a formal information sharing through a TLP-governed Threat Sharing Hub. We align with the Traffic Light Protocol (TLP:CLEAR, GREEN, AMBER, RED).
- We support both human-readable intelligence and STIX-formatted data exchange for structured sharing, giving you a lightweight sharing option or a powerful STIX upload.
- We also include audit logs and optional sharing agreements/NDA templates for governance and traceability.
Your Business Advantage
- Yours/Ours customers can prove participation in trusted intelligence-sharing communities — a DORA requirement.
- Reduces internal overhead, ThreatInsights handles the compliance, logging, and safe sharing automatically.
- Helps you build confidence with regulators and partners by demonstrating a mature threat-intelligence process.
Articles 24–27 — Threat-Led Penetration Testing (TLPT)
How ThreatInsights Meets It
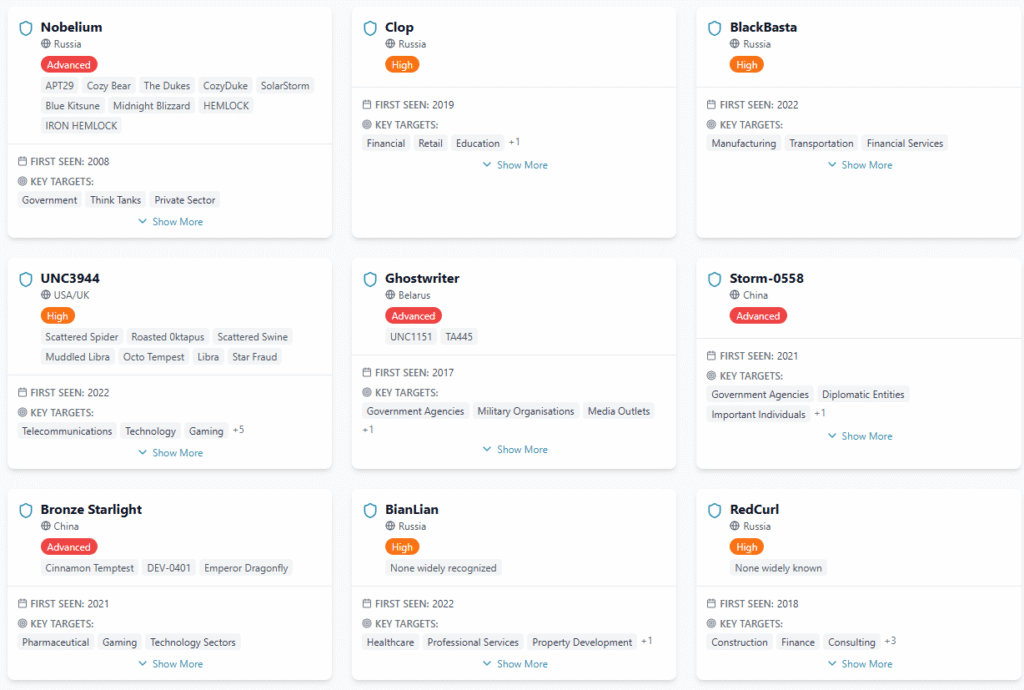
- We supply external attacker profiles, TTPs, and sector-specific threat scenarios for use in TLPT exercises (TIBER-EU/CBEST-style).
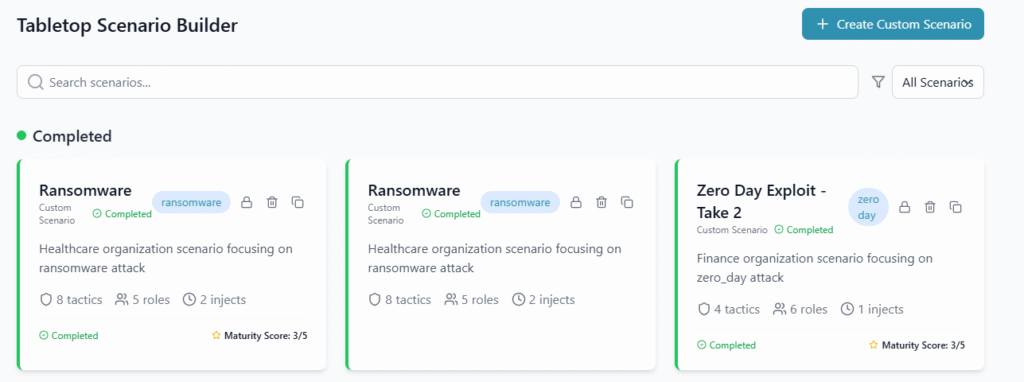
- We integrate MITRE ATT&CK mapping, through our Threat Actor Catalogue, and incorporate that into our Scenario Builders to simulate realistic adversary behaviour.
- Optionally we can also link CTI findings directly into Penetration Test planning or table-top exercises.
Your Business Advantage
- Enables you to run intelligence-led testing aligned with regulator expectations.
- Provides your business with a documented evidence that TLPT scenarios are based on verified external threat intelligence.
Articles 19–22 — Incident Reporting and Communication with Authorities
How ThreatInsights Meets It
- We deliver Incident Readiness Playbooks, Response Runbooks, and Notification Templates designed around DORA reporting timelines.
- We support simulated incident drills and table-top exercises for leadership teams. Build and save your templates, re-run whenever you need to.
- Generates audit evidence and reporting templates that can be directly used for DORA or NIS2 disclosures.
Your Business Advantage
- Your businesses can respond faster, report correctly, and avoid penalties for late or incomplete notifications.
- It helps you converts compliance requirements into repeatable, evidence-ready processes inside the portal.
Article 8–10 — Risk Management Framework & Continuous Monitoring
How ThreatInsights Meets It
- Our Continuous Attack Surface Management monitors external assets for new vulnerabilities, open services, shadow IT, and exposed data.
- We offer Third-Party Risk Monitoring to track supplier exposure which is another DORA obligation.
- All our findings are human-verified to eliminate false positives and “alert fatigue.” Which is pretty cool right?
Your Business Advantage
- Provides you with continuous situational awareness of the organisation’s attack surface.
- Helps you prove and evidence proactive risk management for regulatory reviews or audits.
- We help you reduce noise, especially for smaller/limited teams so they can focus on the threats that matter most.
Article 45 (again) — Governance, Legal & GDPR-Safe Sharing
How ThreatInsights Meets It
- Our built-in TLP governance ensures each briefing is labelled for correct distribution.
- We have optional anonymisation for sensitive submissions.
- Our platform provides GDPR-compliant data handling, encryption, and access controls.
- We also have optional sharing agreements, community rules, and NDAs supplied through the platform.
Your Business Advantage
- Our customers, your clients can join intelligence-sharing initiatives without the legal burden of building their own framework.
- Our ready ready-made compliance documentation simplifies regulatory submissions.
- Shows to regulators a clear governance process for threat intelligence handling.
Article 13 & 14 — Operational Resilience and Preparedness
How ThreatInsights Meets It
- Our platform combines Threat Intelligence, Attack Surface, and Incident Readiness data all through on intuitive platform.
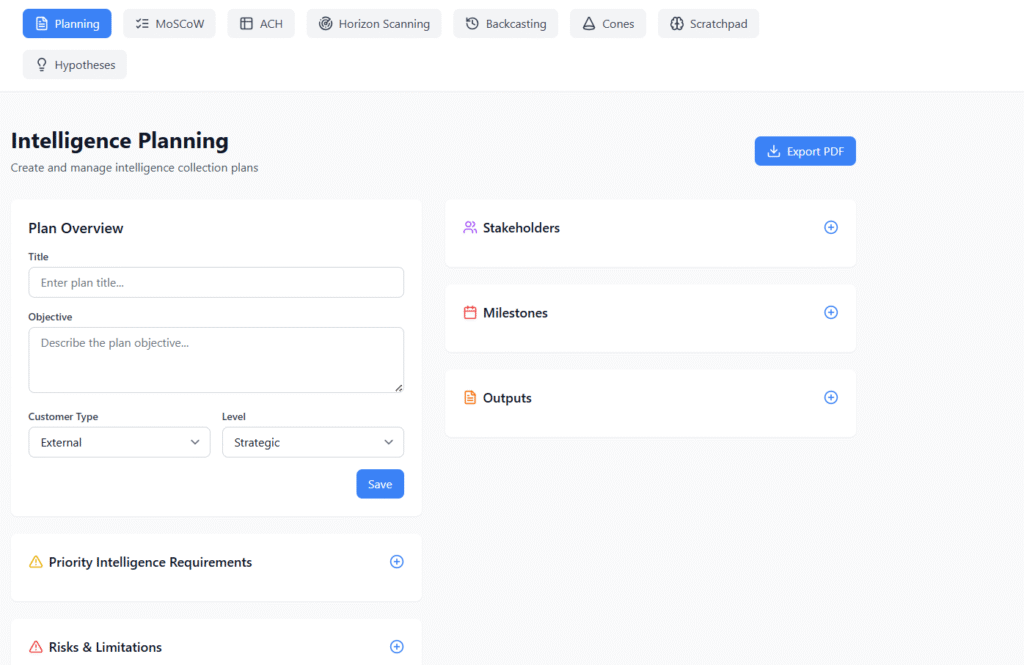
- We provides scenario planning tools (Horizon Scanning, Cones of Plausibility, Backcasting) to anticipate future risks, great if you have Threat analysts in your team.
- We also offer quarterly threat landscape reports mapped to business impact.
Your Business Advantage
- We turn threat intelligence into actionable resilience planning for your business.
- Our platform helps your management demonstrate a proactive rather than reactive resilience stance.
- We reduce reduces consulting cost massively, these functions are built into the SaaS platform and you get the right advice when you need it.
ThreatInsights gives financial entities everything they need to meet DORA’s threat intelligence and resilience requirements combining real threat data, controlled sharing, and built-in compliance evidence all in a single, accessible platform
We like to think we’ve done a pretty solid job at creating our platform to meet these requirements. If you want more details or a demonstration of how your business can benefit then contact us and we’ll be more than happy to set something up.
Error: Contact form not found.