See what the attackers see
AND SHUT IT DOWN
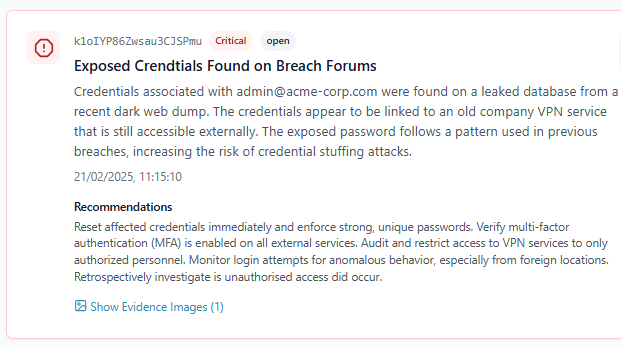
Our ASM module continuously scans your digital footprint to identify exposed assets, forgotten subdomains, and shadow infrastructure. With prioritized risks and clear remediation paths, we help you reduce your attack surface and stay one step ahead of opportunistic threats.
Complete Attack Surface Visibility
Gain comprehensive visibility into your external attack surface with continuous monitoring, intelligent risk assessment, and actionable remediation guidance.
Continuous Asset Discovery
Automatically discover and catalog all your digital assets across domains, subdomains, and cloud infrastructure
Exposed Asset Identification
Identify publicly accessible services, open ports, and misconfigured systems that attackers could exploit
Shadow IT Detection
Uncover forgotten subdomains, abandoned applications, and unauthorized cloud resources
Risk Prioritisation
Intelligent scoring system that prioritizes risks based on exploitability and business impact
Remediation Guidance
Clear, actionable steps to secure identified vulnerabilities and reduce your attack surface
Real-time Monitoring
Continuous monitoring for changes in your attack surface with instant alerts for new exposures
Why Attack Surface Management Matters
Your attack surface is constantly evolving. New assets, configuration changes, and forgotten systems create opportunities for attackers. Stay ahead with continuous monitoring and proactive risk management.
-
Reduce unknown exposures Discover and secure assets you didn't know existed
-
Prevent Data Breaches Identify and fix vulnerabilities before attackers find them
-
Improve security posture Continuously monitor and improve your external security stance
-
Streamline remediation Get clear, actionable guidance to fix identified issues
Ready to See Your Attack Surface?
Don’t let unknown assets become your biggest security risk. Start monitoring your attack surface today and stay ahead of threats with continuous visibility and proactive risk management.
